----------------------------------------------------------------------------
IPSEC VPN Configuration between Juniper & CISCO Router:
----------------------------------------------------------------------------
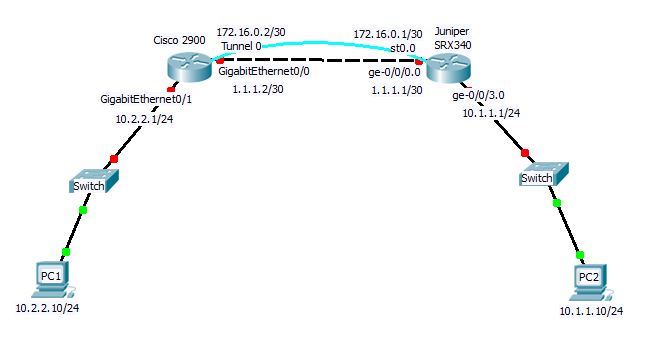
SRX340-A: Untrust IP- 1.1.1.1/30, Trust IP-10.1.1.1/24, st0.0 IP: 172.16.0.1/30
CISCO-B: Untrust IP- 1.1.1.2/30, Trust IP-10.2.2.1/24, tunnel 0 IP:172.16.0.2/30
##Juniper Site-A:
set interfaces ge-0/0/0 unit 0 family inet address 1.1.1.1/30
set interfaces ge-0/0/3 unit 0 family inet address 10.1.1.1/24
set interfaces st0 unit 0 family inet address 172.16.0.1/30
set interfaces st0 unit 0 family inet mtu 1400
set security zones security-zone trust interfaces st0.0
set security zones security-zone trust interfaces ge-0/0/3.0
set security zones security-zone untrust interfaces ge-0/0/0.0
Phase 01 for Site "A":
---------------------------------
## IKE proposal
set security ike proposal IKE-Proposal lifetime-seconds 28800
set security ike proposal IKE-Proposal authentication-method pre-shared-keys
set security ike proposal IKE-Proposal authentication-algorithm sha1
set security ike proposal IKE-Proposal encryption-algorithm aes-128-cbc
set security ike proposal IKE-Proposal dh-group group2
## IKE policy
set security ike policy IKE-Poly mode main
set security ike policy IKE-Poly proposals IKE-Proposal
set security ike policy IKE-Poly pre-shared-key ascii-text tawfique
## IKE gateway with peer IP address, IKE policy and outgoing interfac
set security ike gateway IKE-GW ike-policy IKE-Poly
set security ike gateway IKE-GW address 1.1.1.2
set security ike gateway IKE-GW external-interface ge-0/0/0.0
## Security zones, assign interfaces to the zones & host-inbound services for each zone
set security zones security-zone Untrust host-inbound-traffic system-services ike
Phase 02 for Site "A":
----------------------
## IPSec proposal
set security ipsec proposal IPSEC-Proposal lifetime-seconds 3600
set security ipsec proposal IPSEC-Proposal protocol esp
set security ipsec proposal IPSEC-Proposal authentication-algorithm hmac-sha1-96
set security ipsec proposal IPSEC-Proposal encryption-algorithm aes-128-cbc
## IPSec Policy
set security ipsec policy IPSEC-Poly proposals IPSEC-Proposal
## IPSec VPN
set security ipsec vpn IPSEC-VPN bind-interface st0.0
set security ipsec vpn IPSEC-VPN ike ipsec-policy IPSEC-Poly
set security ipsec vpn IPSEC-VPN ike gateway IKE-GW
set security ipsec vpn IPSEC-VPN establish-tunnels immediately
#Routing Option
set routing-options static route 10.2.2.0/24 next-hop st0.0
##CISCO Site-B:
Router(config)#interface GigabitEthernet0/0
Router(config-if)#ip add 1.1.1.2 255.255.255.252
Router(config-if)#no sh
Router(config)#interface GigabitEthernet0/1
Router(config-if)#ip add 10.2.2.1 255.255.255.0
Router(config-if)#no sh
Phase 01(IKE isakmp configuration)
----------------------------------
Router(config)#crypto isakmp policy 1
Router(config-isakmp)#authentication pre-share
Router(config-isakmp)#encryption aes 128
Router(config-isakmp)#hash sha
Router(config-isakmp)#lifetime 28800
Router(config-isakmp)#group 2
Router(config-isakmp)#exit
Router(config)#crypto isakmp key tawfique address 1.1.1.1
Phase 02(IPsec VPN configuration)
----------------------------------
Router(config)#crypto ipsec transform-set MY-VPN esp-aes 128 esp-sha-hmac
Router(cfg-crypto-trans)# mode transport
#create IPsec profile
Router(config)#crypto ipsec profile VPNPROFILE
Router(ipsec-profile)# set transform-set MY-VPN
#create tunnel interface with IP and give IPsec protection
Router(config)#interface tunnel 0
Router(config-if)#ip add 172.16.0.2 255.255.255.252
Router(config-if)#tunnel source 1.1.1.2
Router(config-if)#tunnel destinations 1.1.1.1
Router(config-if)#tunnel mode ipsec ipv4
Router(config-if)#tunnel protection ipsec profile VPNPROFILE
Router(config-if)#ip mtu 1400
#create static route
Router(config)#ip route 10.1.1.0 255.255.255.0 tunnel 0
------------------------------------------
#Verifying the VPN for Juniper:
------------------------------------------
1) show security ike security-associations
2) show security ipsec security-associations
3) show security ipsec statistics
4) show route
------------------------------------------
#Verifying the VPN for Cisco:
------------------------------------------
1) show crypto isakmp sa
2) show crypto ipsec sa
3) show crypto ipsec statistics
4) show route
Phenomenal !
ReplyDeleteThis comment has been removed by the author.
ReplyDelete